| Thursday, November 14, 2002 |
21:50 - Virii
http://www.denbeste.nu/cd_log_entries/2002/11/Virusmarketing.shtml
|
(top)  |
Steven Den Beste has a post which claims that the lack of viruses on the Mac is a sociological/economical phenomenon, rather than a technical one.
I'd rather not get into the speculation over things like the vulnerability of OS9 and prior releases to viruses, other than to mention that the biggest risk in a virus lies in its ability to propagate itself, which in Windows manifests as a gleeful romp through Outlook and IE and IIS (after all, I'm sure Klez does a whole lot more damage in simple dental chafing over how many times it appears in people's inboxes, rather than in actual damage to people's systems). The Mac OS, while potentially more fragile in its memory structure, was much less likely to be exposed to worm-style exploits because the Mac lacked badly-written and widely-used vectors like Outlook. But that's a separate issue.
I just wanted to clarify something:
MacOSX is protected against that if properly used, as is WinNT/2K/XP. Of course, if a user routinely runs with an administrator account, they discard this protection. I don't. I have an administrator account on my Win2K systems which I use when need be, such as to do installations, but I routinely run with a "Power User" account, which does not permit me to seriously damage the system by mistake. I do that deliberately. I'm not a fool and I don't generally do things which are harmful, but this represents a level of protection that I choose to use, in part because it protects me from hostile programs which actually do end up fooling me. Unfortunately, a lot of people have gotten in the habit of routinely using an administrator account and by so doing they are throwing away one of the best protections their systems give them, to protect them against the actions of those who write hostile programs, even for OSX.
You can't discard this protection in OS X, though.
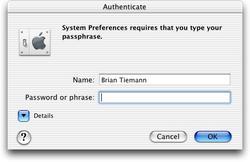
The fact is that unless you go under the hood and perform some serious monkey-wrench tweaking, you cannot log in with an administrator or "root" account in OS X. Admin security in OS X is done via the "sudo" model, in which any system-altering action (such as new software installations, modifying file permissions/ownership, or the unlocking of system-wide preferences that you have locked) must be authenticated by a designated admin user (of which there can be more than one) entering his own password. This establishes that the person who is using the current login session is the rightful owner of that account, and has the rights to perform an administrator-level action. (Non-admin users, by the way, can install software and such from within their own login sessions-- by entering an admin user's username and password.) It's on-demand action-level security, not session-level security (which, by the way, is prone to hijacking by malicious local users if the rightful user leaves himself logged in). Each unique action is assumed insecure and prompts for admin authentication. System preferences which alter global settings are unlocked at login time for admin users, but can be locked again at any time. Thus, the "root password" is irrelevant (the root account can't be accessed in the default installation, even from the command line), and for any new and potentially system-altering action, the user is given a challenge to prove he's a trusted admin, and a psychological reminder that the requested action is potentially dangerous (which may in fact be the more important benefit).
I've written our project-management system at work based on this model. Any data can be viewed by anybody; but anytime a user attempts to execute a data-altering command, he is prompted for a login and password. This has the dual effect of authenticating the user and making the user think twice about what he's doing. It's prevented a huge number of user errors that were a matter of daily maintenance to fix in our earlier system, which happily and transparently accepted any data-altering action from any user who had logged-in and authenticated once upon starting the client app.
The fact that so many people choose to run their Windows machines via administrator accounts is a symptom of the "convenience and security are orthogonal goals" axiom; if the system makes it unnecessarily inconvenient to operate in a secure manner (e.g. by running as a standard user and only using the admin account when absolutely necessary, or by using a "Power User" account, which offers limited admin power), then the user will choose to operate in a less secure manner (e.g. using an administrator account for day-to-day computing). Logging in and out of desktop sessions is inconvenient, and, today, something a user rarely wants or needs to do. If admin tasks are not made a part of the standard and convenient workflow (as OS X and best-practices UNIX server platforms do it), then users will make them part of their standard and convenient workflow, regardless of the risk involved.
Whether OS X is or is not inherently more or less porous than Windows is, again, a side issue. The crux of this particular point (granted, only one part of the larger thesis) is, however, based on the assumption that OS X admin security is done on the same asking-for-trouble model that Windows uses-- and that isn't the case.
|
|