| Sunday, March 10, 2002 |
22:18 - Oh, this one's priceless...
|
(top) 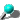 |
<sings like the Squirrel Nut Zippers> There's a spam goin' round in town, spreading lies...
This one's really quite fun, and well-constructed in that way that fools people into thinking it's legit. What's so funny is the places where it's so clearly fake, places that are really quite obvious-- where even newbies should be made suspicious.
From: "Microsoft Corporation Security Center" <rdquest12@microsoft.com>
Date: Sun Mar 10, 2002 09:32:10 PM US/Pacific
To: "Microsoft Customer" <'customer@yourdomain.com'>
Subject: Internet Security Update
Reply-To: <rdquest12@microsoft.com>
"customer@yourdomain.com", huh? And what sounds legit about "rdquest12@microsoft.com"? Ah well, I'm not prepared to guess.
Microsoft Customer,
What'd you call me?
this is the latest version of security update, the known security vulnerabilities affecting Internet Explorer and MS Outlook/Express as well as six new vulnerabilities, and is discussed in Microsoft Security Bulletin MS02-005. Install now to protect your computer from these vulnerabilities, the most serious of which could allow an attacker to run code on your computer.
Description of several well-know vulnerabilities:
- "Incorrect MIME Header Can Cause IE to Execute E-mail Attachment" vulnerability. If a malicious user sends an affected HTML e-mail or hosts an affected e-mail on a Web site, and a user opens the e-mail or visits the Web site, Internet Explorer automatically runs the executable on the user's computer.
- A vulnerability that could allow an unauthorized user to learn the location of cached content on your computer. This could enable the unauthorized user to launch compiled HTML Help (.chm) files that contain shortcuts to executables, thereby enabling the unauthorized user to run the executables on your computer.
- A new variant of the "Frame Domain Verification" vulnerability could enable a malicious Web site operator to open two browser windows, one in the Web site's domain and the other on your local file system, and to pass information from your computer to the Web site.
- CLSID extension vulnerability. Attachments which end with a CLSID file extension do not show the actual full extension of the file when saved and viewed with Windows Explorer. This allows dangerous file types to look as though they are simple, harmless files - such as JPG or WAV files - that do not need to be blocked.
Wow. Well-researched, citing security bulletins and documented exploits, and warning against viruses and trojans. This has gotta be legit! They're trying to fight viruses! See-- it says right here!
You know how many people's cars get broken into every year by employees of car dealerships and aftermarket parts shops who the cars' owners paid to install security systems? The tech would just install the alarm or locking stuff, and keep a copy of the key for himself?
Nah, most people don't know, most likely. Which is why this virus will infect lots of people.
System requirements:
Versions of Windows no earlier than Windows 95.
This update applies to:
Versions of Internet Explorer no earlier than 4.01
Versions of MS Outlook no earlier than 8.00
Versions of MS Outlook Express no earlier than 4.01
How to install
Run attached file q216309.exe
Okay, this is what gets me. If you're trying to pass yourself off as Microsoft, even in an e-mail (a completely ludicrous medium for dispensing security updates, for many reasons beyond the implicit assumption that everybody in the world that receives the e-mail is a Microsoft customer), why would you name your attachment "q216309.exe"? Why not, oh, I don't know, "Microsoft Security Update 03-10-02.exe"?
How to use
You don't need to do anything after installing this item.
Yeah, I'll bet.
For more information about these issues, read Microsoft Security Bulletin MS02-005, or visit link below.
http://www.microsoft.com/windows/ie/downloads/critical/default.asp
If you have some questions about this article contact us at rdquest12@microsoft.com
Thank you for using Microsoft products.
Yuh-huh. More citings of published security bulletins (whether real or not-- I don't know; it'd be good enough for me if I were in the sights of this virus for real), and even a link to the real live security-update site for IE. How convenient and helpful.
With friendly greetings,
MS Internet Security Center.
Ah-hah! "With friendly greetings". You know what that says? East Asia. From my experience, this is the kind of salutation you put on a letter there, but you'd never see a native English speaker end a letter like this. Especially not a Microsoft customer service agent.
----------------------------------------
----------------------------------------
Microsoft is registered trademark of Microsoft Corporation.
Windows and Outlook are trademarks of Microsoft Corporation.
For that ultra-convincing flourish.
Now, this is just what you get when picking apart the body of the message itself. The headers, as should surprise nobody, reveal that the message comes through "molly.intercom.net" and "pfuckie (a129.intercom.net [216.240.100.29])". But who looks at headers?
I haven't been able to find the ID for the virus (I'm assuming it's a virus, and I'd be very very surprised if it weren't) at mcafee.com, largely because they seem to have made it difficult beyond imagination to browse recent virus alerts; yeah, real responsible, guys. But I'd wager that this little beauty's going to be fooling all kinds of people as it makes its rounds.
It's not anywhere near as beautifully crafted as the "I send you this file to have your advice" thing (which I still get about 20 copies of per week), or Nimda, but it's quite a piece of work nonetheless.
On the extremely unlikely chance that you read this blog entry before you open your e-mail with this in it, be-thee-ware.
|
|